Securing the Ship: Navigating Container Vulnerabilities and their Mitigation

Containers have revolutionized application deployment, offering scalability and efficiency. However, they also introduce unique security risks that attackers can exploit. Common vulnerabilities include running containers with excessive privileges, outdated base images with known CVEs (Common Vulnerabilities and Exposures), and misconfigured networking that exposes sensitive workloads. A compromised container can become an entry point for attackers to move laterally, escalate privileges, or exfiltrate data. Without proper security controls, containerized applications can become just as—if not more—vulnerable than traditional workloads.
One practical way to mitigate container security risks is by enforcing the principle of least privilege and scanning for vulnerabilities in base images. For example, in a Kubernetes environment, you can restrict container privileges using a Security Context or implement broader policies with Pod Security Admission (PSA).
Pod Security Admission (PSA) is a built-in Kubernetes admission controller that replaced Pod Security Policies (PSP) (deprecated in Kubernetes 1.21, removed in 1.25). PSA validates pod specifications against predefined security standards—Privileged, Baseline, and Restricted—helping you enforce security rules at the cluster level without complex third-party tooling.
Using Security Contexts for Fine-Grained Controls
The Security Context allows you to define security settings directly in your pod specifications. Below is a Kubernetes YAML snippet that ensures containers run as a non-root user and have read-only access to the filesystem:

This configuration prevents privilege escalation, ensures the container runs as a non-root user, and restricts filesystem modifications—reducing the risk of an attacker gaining control over the container. The phrase ‘prevents privilege escalation’ refers to a setting that controls whether a process can gain more privileges than its parent process. This directly controls whether the no_new_privs flag gets set on the container process. allowPrivilegeEscalation is always true when the container:
• is run as privileged, or
• has CAP_SYS_ADMIN
Using Pod Security Admission (PSA) for Policy Enforcement
To systematically enforce security controls across your cluster, you can configure Pod Security Admission by defining security standards at the Namespace level. For instance, to enforce the Restricted policy (the most secure level), you would label your namespace like this:
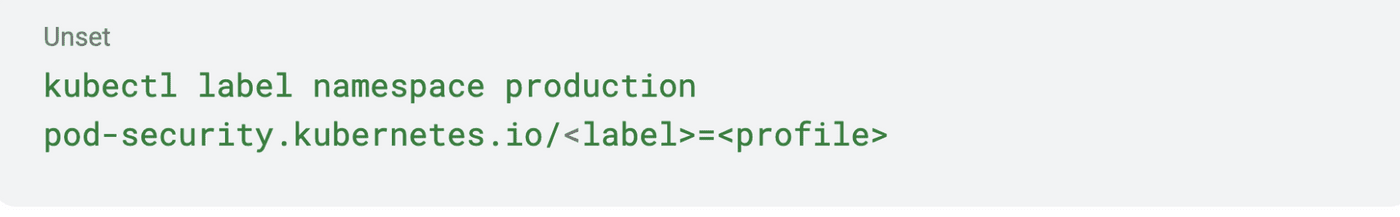
With this label:
• enforce: Blocks pods that violate the policy from being created.
• audit: Logs warnings for violating pods (useful for monitoring).
• warn: Returns warnings to users during pod creation.
The Restricted profile mandates:
• Running as a non-root user
• Disabling privilege escalation
• Mounting filesystems as read-only by default
• Dropping dangerous Linux capabilities
By using Pod Security Admission, Kubernetes helps you enforce security best practices without requiring third-party solutions, reducing the risk of misconfigurations slipping through unnoticed.
Implementing robust security measures in Kubernetes environments is crucial to protect against potential threats. Third-party policy tools like Kyverno and Open Policy Agent (OPA) with Gatekeeper enhance Kubernetes' native security features by providing dynamic policy enforcement capabilities. Additionally, configuring Pod Security Admission (PSA) effectively is vital for maintaining a secure and compliant cluster, especially in complex environments.
Configuring Pod Security Admission (PSA) for Complex Environments
Pod Security Admission is a built-in admission controller in Kubernetes that enforces Pod Security Standards at the namespace level. Configuring PSA effectively in complex environments requires careful planning:
1. Assess Security Requirements: Determine the appropriate security level—Privileged, Baseline, or Restricted—for each namespace based on workload sensitivity.
2. Label Namespaces: Apply the relevant PSA labels to each namespace to enforce the desired security standards. For example:
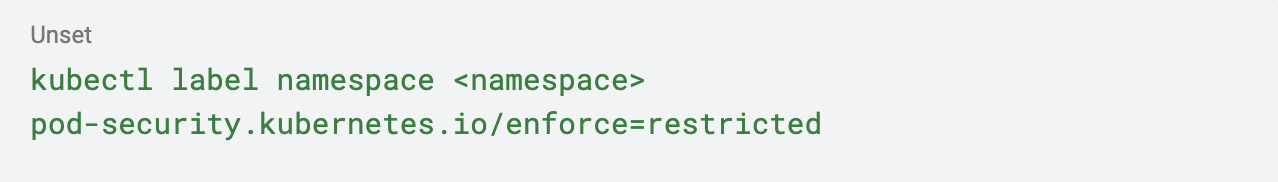
3. Use Exemptions for Flexibility: In complex environments, certain workloads may require exemptions from specific policies. PSA allows for exemptions based on usernames, runtime classes, or namespaces. Configure these exemptions carefully to balance security and functionality.
4. Implement Audit and Warn Modes: Before enforcing policies, use the audit and warn modes to identify potential violations without impacting workloads. This approach helps in fine-tuning policies:
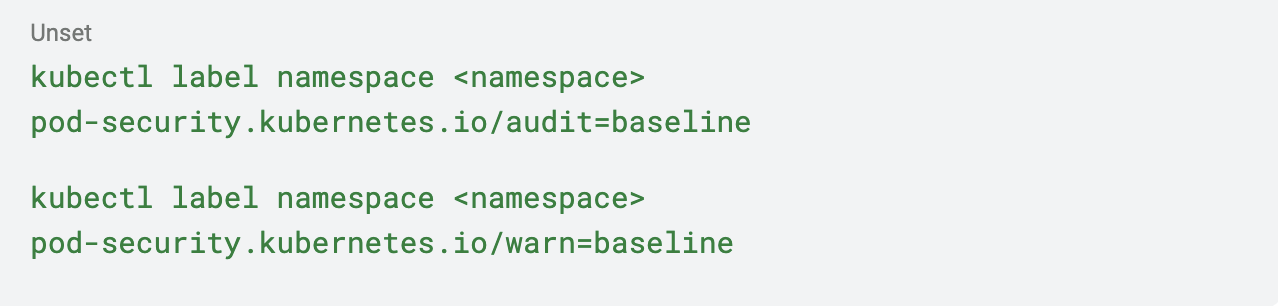
5. Continuous Monitoring and Updates: Regularly review and update PSA configurations to adapt to evolving security requirements and emerging threats.
A Layered Defense Approach
Container security should follow a defense-in-depth approach, combining multiple strategies:
Image Security: Regularly scan container images for vulnerabilities (e.g., with Trivy or Grype).
Network Segmentation: Use NetworkPolicies to limit container-to-container communication.
RBAC and Least Privilege: Limit cluster access and container permissions.
Runtime Monitoring: Use tools like Falco to detect suspicious runtime behavior.
Pod Security Admission: Automate policy enforcement at the namespace level.
By thoughtfully layering these security controls, organizations can significantly reduce their container attack surface and build more resilient, secure infrastructure.
Secure your business, not just your infrastructure – Get the Cloud Security Strategy Blueprint.




